These lying idiots at Dominion were running an exploitable Serv-U FTP server on their public-facing dvsfileshare.dominionvoting.com IP address. When they got caught, they took place in a 17-hour cover-up operation. They initially took their page down, then edited it so it didn’t show the SolarWinds name, just leaving Serv-U (but the morons left it in the page source code), then later they removed even the Serv-U portion, but still again left SolarWinds in the page source code (they weren’t smart enough to remove it entirely). If they can’t even figure out how to cover their tracks on something this simple, they have no business writing software to handle our elections. Not to mention, innocent people DO NOT TRY TO CONCEAL THINGS LIKE THIS!

Then everyone freaked out because of the SolarWinds Orion Platform hack and Dominion misdirected all the pleebs at that and then claimed they don’t use Orion. What the pleebs didn’t realize is that there was ALSO a zero-day exploit on the Serv-U ‘FTP’ software that Dominion was using up until and at that time, and they bought the BS from Dominion, hook, line, and sinker. Nobody that falls for this should be using electronic voting systems (or much less, anything electronic). I don’t mean to come down on those deceived by Dominion, but at some point they do need to take responsibility for not having enough knowledge to protect a domain that they claim to be responsible or making decisions for. It is UNFAIR to put them in these positions, but it is important to notify them that they ARE in these positions so they can’t claim ignorance after being put on friendly notice.
So let’s walk through it. First, sometimes people at Dominion are honest, and I am happy to point that out when I see it.
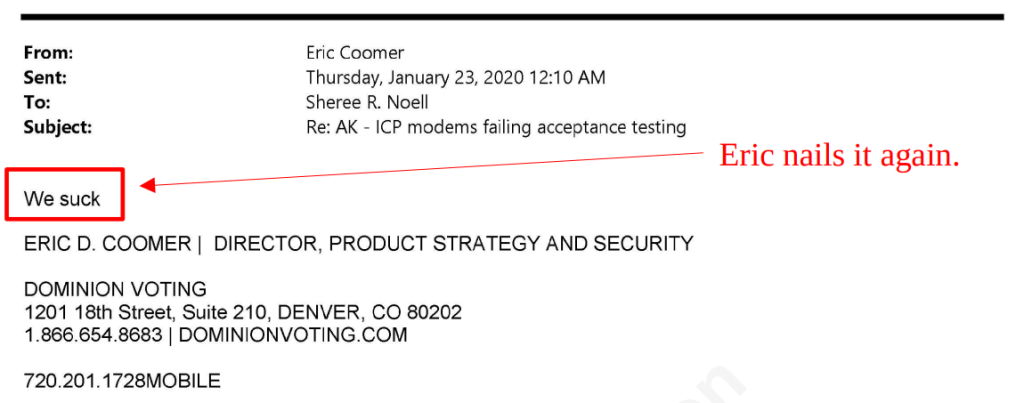
Eric is not a stupid person by any means. I do wish he used his intelligence to help his fellow man, though.
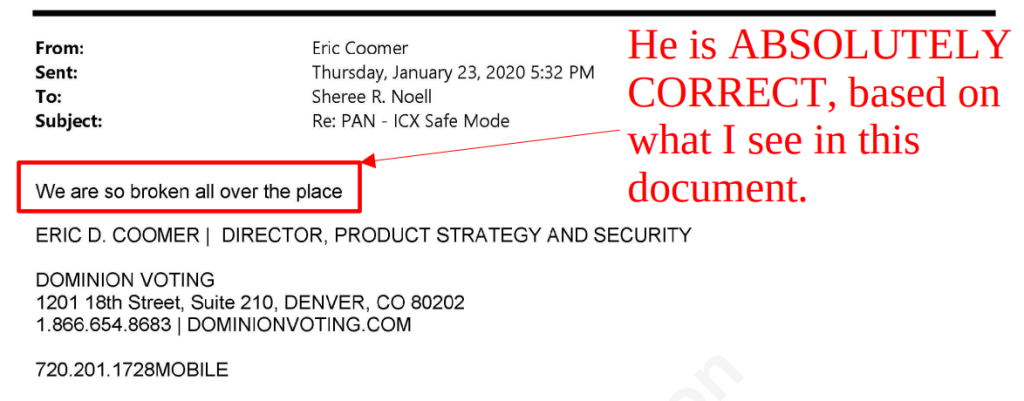
Based on the evidence I have seen that clearly Eric knows about, as he is listed as a sender and/or recipient of many of the emails that shed a bright light on what is going on inside Dominion that those who blindly trust them don’t know about, Eric Coomer’s conclusion in the above email is very accurate.
Let’s begin with the information regarding this particular Zero-Day Exploit directly from SolarWinds themselves: https://www.solarwinds.com/trust-center/security-advisories/cve-2021-35211 (PDF Serv-U-Remote-Memory-Escape-Vulnerability.pdf)
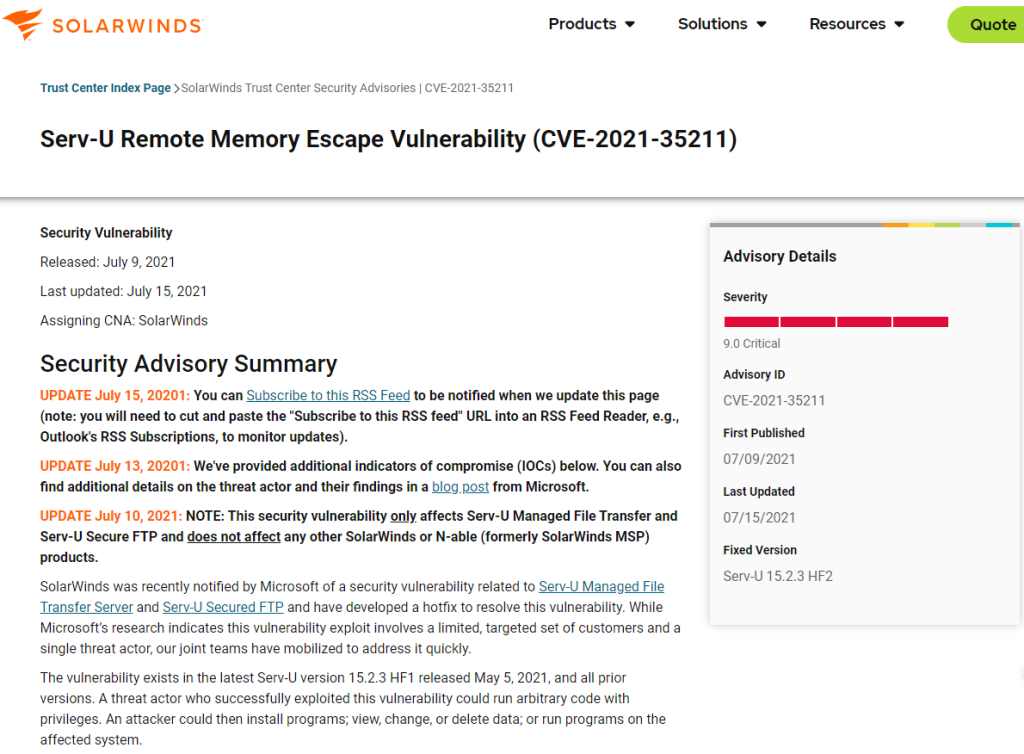
Another site: SolarWinds patches critical Serv-U vulnerability exploited in the wil_ – www.bleepingcomputer.com.pdf
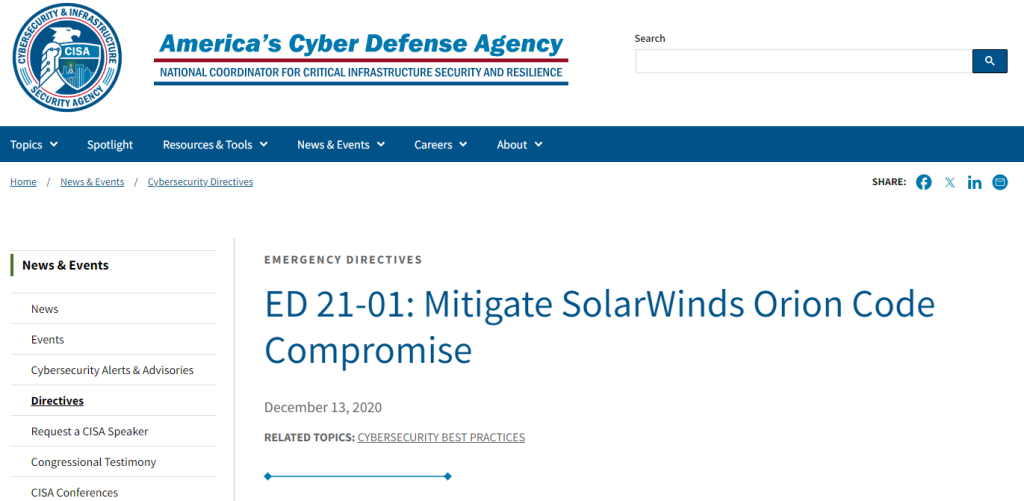
On December 13, 2020, CISA the Cybersecurity & Infrastructure Security Agency charged with keeping our elections secure, came out with this:
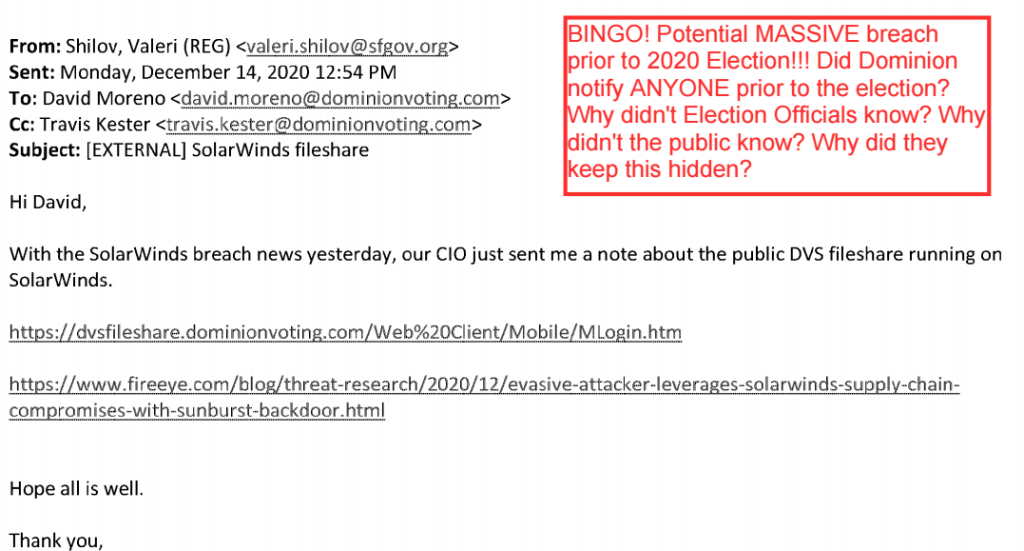
Valeri Shilov (IT Operations Support in San Francisco CA) sent an email to David Moren and Travis Kester of Dominion Voting Systems regarding Dominion’s public fileshare running on SolarWinds:
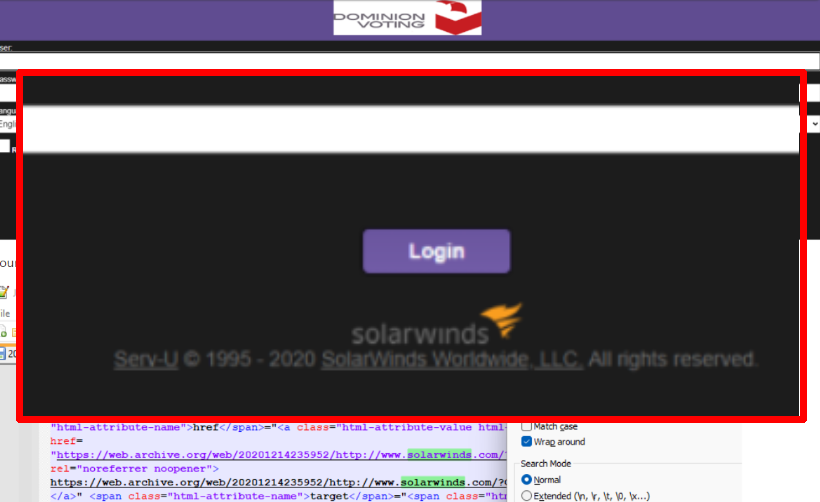
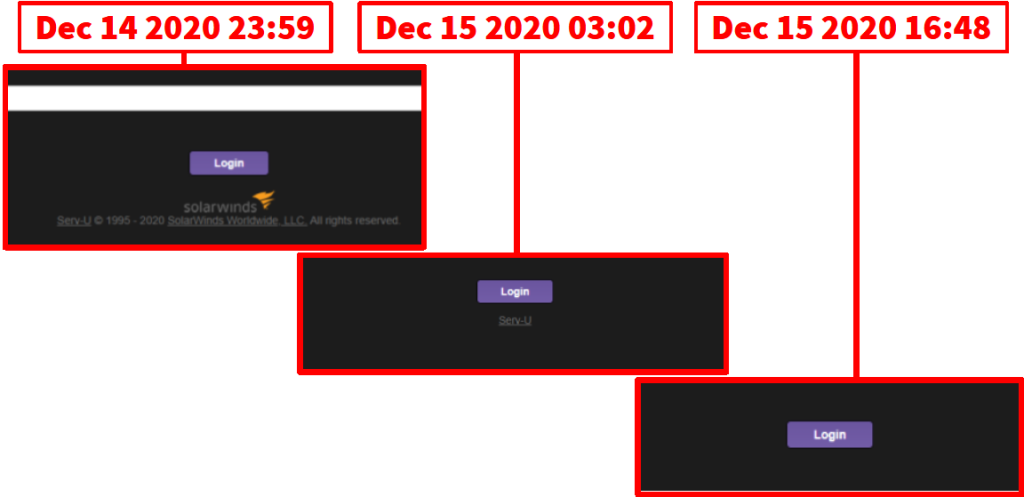
December 14, 2020 23:59, prior to the cover-up, their public file-sharing site looked like this:

I’ll zoom in for you:
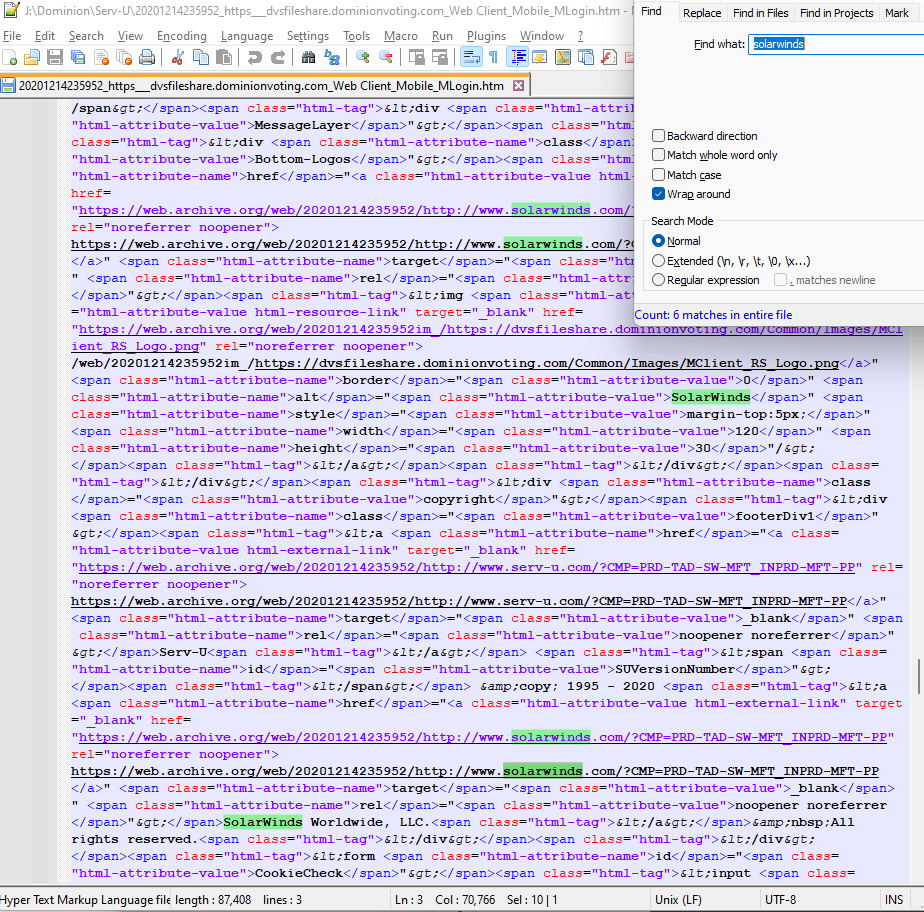
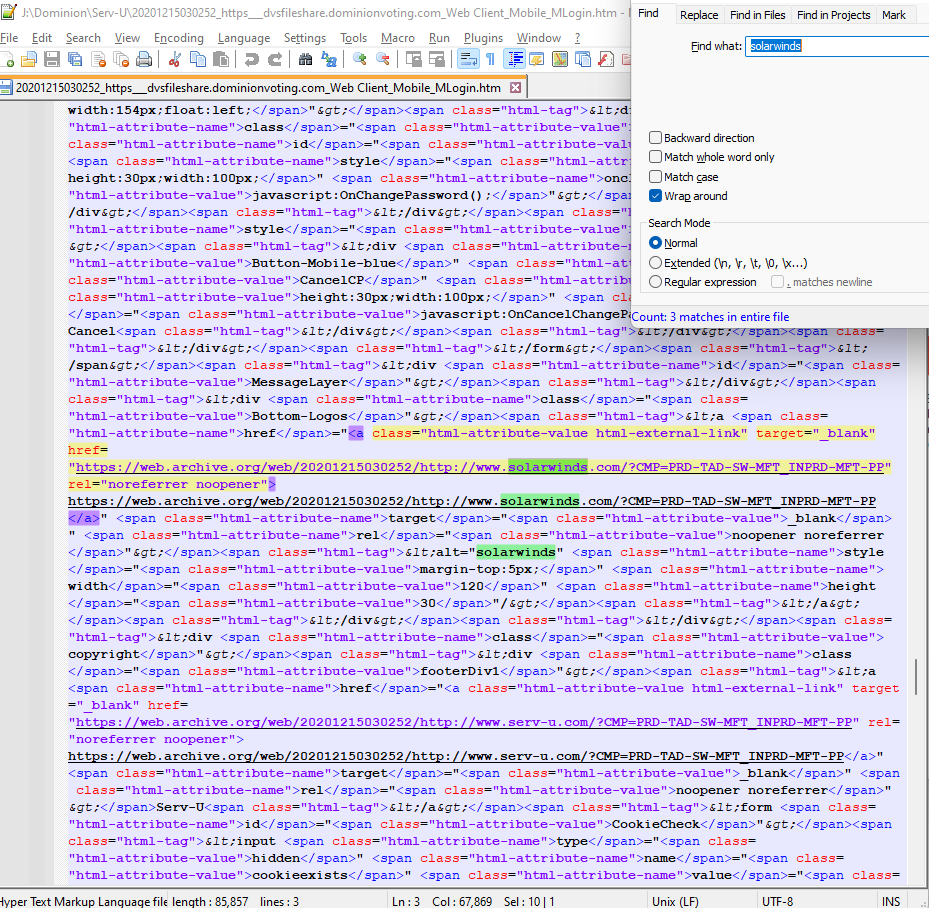
The source code for their website (20201214235952_https___dvsfileshare.dominionvoting.com_Web Client_Mobile_MLogin.htm) also shows SolarWinds, which is responsible for being displayed in what you see just above:
Then sometime before December 15, 2020 01:56, they take the page down:

Then sometime before December 15, 2020 03:02, they remove SolarWinds:

I’ll zoom in again:
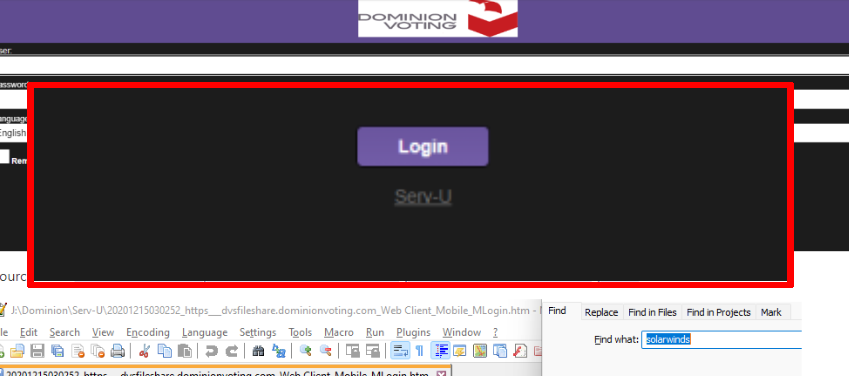
Their website source code (20201215030252_https___dvsfileshare.dominionvoting.com_Web Client_Mobile_MLogin.htm) however, still has remnants of SolarWinds:
Then later in the same day at 16:48, they decide to remove Serv-U to try to cover that up as well:
And again, I’ll zoom in:

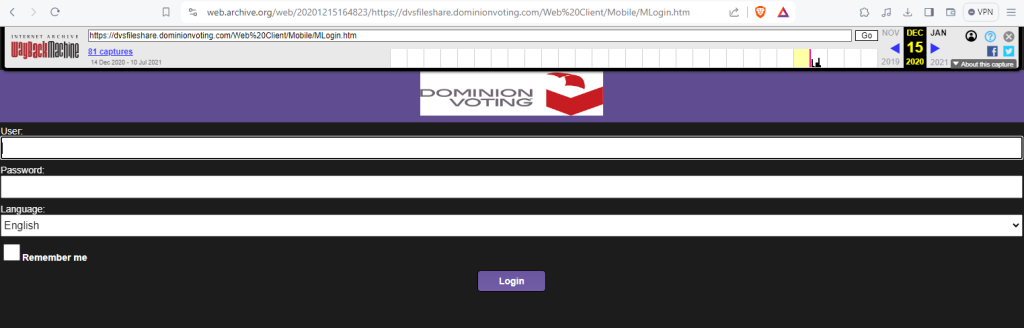
However, their website source code (20201215164823_https___dvsfileshare.dominionvoting.com_Web Client_Mobile_MLogin.htm) still shows SolarWinds everywhere:
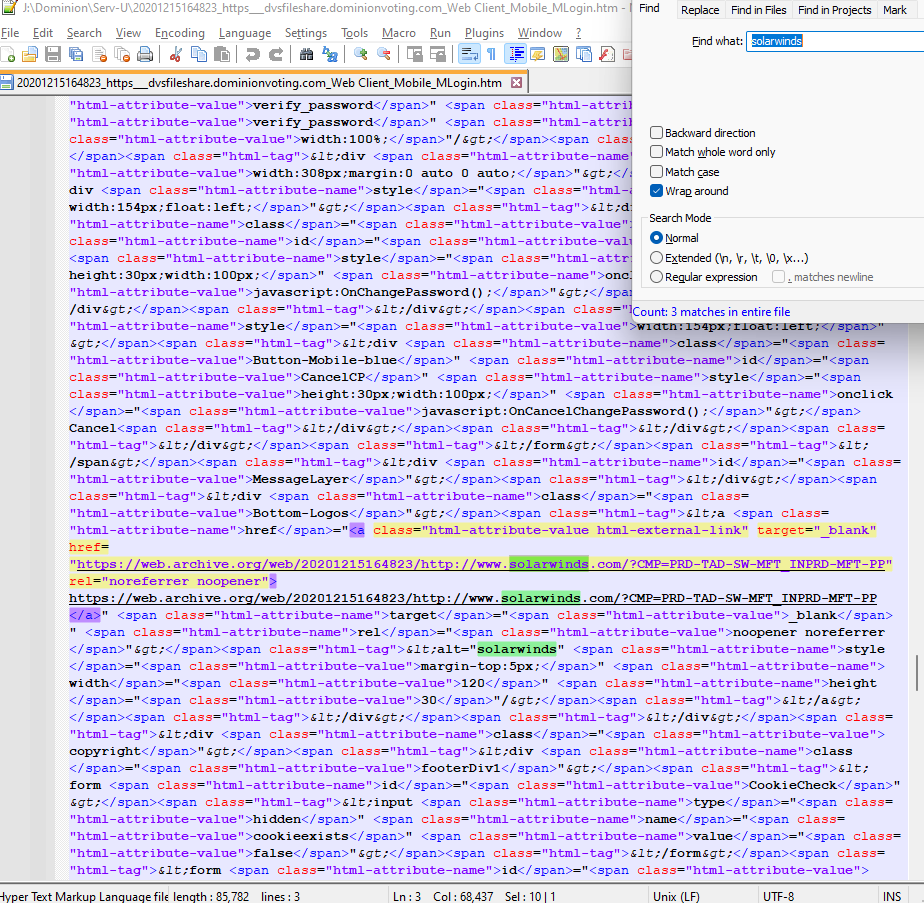
I certainly hope it wasn’t Eric Coomer that was responsible for trying to cover up the fact that they were using SolarWinds Serv-U from the public, because if it was, I guess Eric is including himself in the “we” he claims “sucks”. So in summary, over a 17 hour period:
Dominion, in all the time you spent covering up your use of a compromised product on one of your public-facing file-sharing websites (and you know what files you shared on it), did you notify any government agencies about that? Did you notify any election officials? I would LOVE to ask you a lot more questions as well in a very public setting.



